Beneath, the individual's email address will be revealed. Accepting and sending emails is among the snappiest strategies to communicate via the Internet. Bear as a main priority that each address is the exact same, which means you could send mail to all these to reach the exact same Inbox. Following this progression, you'll be told to your email inbox, where you are able to immediately start sending and getting emails. Additional info found at How to hack an email address.
Other than basic PC information, Email hacking demands creativity and above all, Patience. The hacker may be your girlfriend, sweetheart or on occasion a relative. It is conceivable to wager that each hacker agrees! A Trojan isn't probably going to be successful in recovering a particular account password because it requires the target to install it. The particular thing about keylogger is that anyone with a fundamental understanding of PC should be in a position to install and use it.
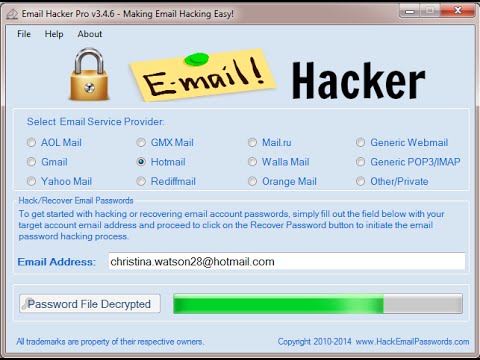
The How to Hack an Email Address Game
SNIFFING If two individuals don't share the identical PC, however share the careful system, one could be able to sniff the others' packets since they sign-on. Utilizing various PCs or many sessions could bring down this to only thousands of years. In case the framework doesn't allow these kind of characters then you may also utilize a letter before the actual answer. Beast FORCE ATTACK many individuals wish to discover software to do an animal power attack. Software exists that may recover the majority of different sorts of locally stored passwords. To guard yourself against Trojans, you shouldn't execute or download software or documents that aren't from a reliable source. Presently at the base of this archive sick incorporate a few connections where you are able to get some crucial tools that may help on your outing during the electronic wilderness.
The one most important aptitude they can learn is the way to utilize their breath. You have to learn a couple of social designing aptitudes that will allow you to casually contact various people groups smartphones. In this manner, in case you're a beginner PC client with a very basic understanding, I recommend utilizing keyloggers as the best technique to hack Yahoo password. An ongoing investigations have found how these two are as a rule increasingly used in a kind of spear-phishing attack.











No comments:
Post a Comment